Published: October 27, 2023
Security 3-2-1 Week of 10/27/23
By Annie articles
3 Interesting Articles
How to ask the board and C-suite for security funding
CSO: Boards of directors are taking on a larger role in cybersecurity funding decisions, emphasizing a culture of corporate cyber responsibility. However, Chief Information Security Officers (CISOs) often face challenges in effectively communicating the technical and financial intricacies of cyber risks to these boards. To bridge this communication gap, CISOs are advised to align their reports with business metrics, collaborate with allies like the CFO and CEO, and clearly illustrate the Return on Investment (ROI) and Total Cost of Ownership (TCO) of security initiatives. Moreover, it’s crucial for CISOs to demonstrate the potential costs of not adopting certain security measures. Tools like the X-Analytics platform can aid CISOs in translating technical needs into business-relevant risks and solutions.
‘Log in with…’ Feature Allows Full Online Account Takeover for Millions
Dark Reading: Flaws in the Open Authorization (OAuth) standard, discovered in online platforms like Grammarly, Vidio, and Bukalapak, could have allowed attackers to hijack millions of user accounts. These vulnerabilities, identified by Salt Labs researchers, suggest many other websites might have similar weaknesses. OAuth is a common cross-platform authentication system, allowing users to log into one site using credentials from another, like Facebook or Google. This series of flaws, described as “Pass-The-Token,” enables attackers to use a token from one site (often one they own) to access another service. For instance, a token from an attacker’s site could be used to log into Grammarly. While these specific vulnerabilities have been addressed by the mentioned platforms, the researchers believe many other websites remain at risk, underscoring the importance of proper OAuth implementation by developers.
Generative AI Can Save Phishers Two Days of Work
Infosecurity Magazine: Generative AI can significantly speed up the process of creating phishing emails, reducing the time taken from 16 hours to just 5 minutes, as highlighted by recent IBM research. In the study, the team aimed to compare the effectiveness of AI-generated phishing emails with those crafted by humans. Using only five prompts, they were able to deceive a generative AI model into producing convincing phishing emails. The expert, with extensive experience in social engineering, found the AI-generated content quite persuasive. Yet, human-crafted emails had a slight edge, garnering a 14% click rate compared to the AI’s 11%. Despite this, there’s a belief that as AI technology evolves, it might eventually surpass human capabilities in this area.
2 Stats You Should Know
It’s expected that the AI software market will expand to $64 billion by 2024, with cybersecurity being the fastest-growing category at a compound annual growth rate of 22.3%. (source)
In the recent survey, 84% of global cybersecurity leaders and decision-makers were very or extremely concerned about the threat of ransomware (vs 76% in 2021). (source)
1 More Thing
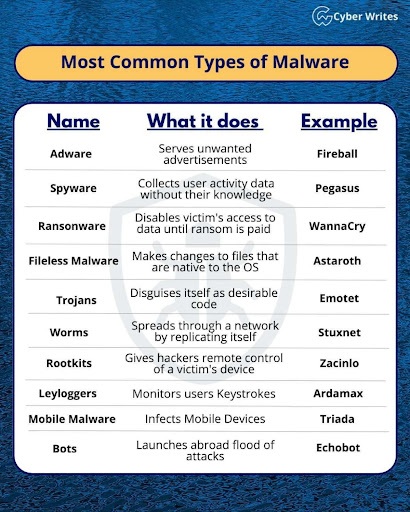
Given that it’s #CybersecurityAwarenessMonth, are you familiar with the most common types of malware? (source)