With the charges against the SolarWinds CISO, effective leadership for infosec and cybersecurity leaders is key to navigating and mitigating risks for an organization. As Electrolux CISO Robert Mungenast noted, “the CISO role is rapidly moving away from the technical side of cybersecurity and into the realm of risk management and business enablement.” In this blog post, we explore this topic by drawing from insights gathered from discussions with over 20 security leaders. We’ll be breaking down the top four qualities essential for success in this field.
Leadership Qualities
Effective leadership in cybersecurity hinges on a blend of distinct yet complementary skills. A leader must possess a broad vision, essential for overseeing the entire scope of cybersecurity and anticipating future challenges. This foresight enables the development of robust defense strategies, grounded in the reality that security incidents are inevitable. Analytical acumen is paramount, as it allows for the intricate dissection of complex issues and the identification of system vulnerabilities. Moreover, strong communication skills are imperative for a leader, facilitating clear and impactful interactions across all levels of the organization. Lastly, a dedication to continuous improvement is vital, driving ongoing evaluation and refinement of cybersecurity practices. Together, these qualities create a resilient and adaptive leader, capable of steering an organization through the evolving landscape of cyber threats.
Organizational Maturity Awareness
Understanding the current maturity level of an organization in handling cyber security is critical. Leaders must evaluate where their organization stands and use a structured approach to communicate this assessment. The progression in improving organizational maturity should follow a “Crawl – Walk – Run” methodology, ensuring gradual and sustainable advancement in managing security risks. Below is an illustration of organizational maturity, exemplified by the Capability Maturity Model Integration (CMMI):
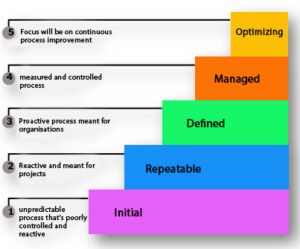
Partnering Across the Organization
In crafting a cybersecurity strategy, communication and collaboration are vital across various organizational levels. For the Board of Directors and Executive Team, clarity reigns supreme; it’s essential to articulate the cybersecurity narrative in a clear, concise manner. This involves the Trio of Transparency: outlining current risks, their potential impact on the business, and the proposed plan of action. A comprehensive Risk Radar should be presented, offering a well-rounded perspective on top risks. Forming alliances, particularly with the CFO and CEO, is also crucial for support and resources.
In legal aspects, attention to RFPs and contracts is key. It’s important to ensure that new contracts undergo a security team review and include specific obligations around critical elements like breach and control failure notifications, compliance obligations, and assessment schedules.
Operational Heads play a pivotal role too. Strategic alignment is necessary, and the approach should be to ask “How” instead of saying “No” to prevent shadow IT. There should be a collective understanding that suppliers are an extension of the organization, adhering to the principle of “Trust but Verify”. Collaboration is necessary for supply chain risk assessments, Business Impact Analyses (BIAs), and Business Continuity and Disaster Recovery (BCDR) processes. Developing hygiene practices for onboarding and offboarding partners, as well as mutual advocacy, are also key components of a robust cybersecurity framework.
Managing Up
Security leaders are the most knowledgeable person in the room regarding digital threats and defense strategies. This expertise is crucial, especially considering Gartner’s prediction in their Top Security and Risk Management trends: “By 2025, 40% of boards of directors will have a dedicated cybersecurity committee overseen by a qualified board member, up from less than 10% today.” This trend underscores the growing recognition of cybersecurity’s importance at the highest levels of governance.
In addition, building strong alliances with key players like the CEO and CFO is vital, as they are instrumental in organizational decision-making and support. Advocacy can be challenging, but presenting data and facts can effectively highlight the inevitability of cybersecurity threats, shifting the narrative from ‘if’ to ‘when’. Once the risks are clearly articulated, it is important to propose practical solutions and request the necessary budget to implement them. This approach not only demonstrates your preparedness but also highlights your proactive stance in addressing potential cybersecurity challenges. By adopting this strategy, you can effectively secure the necessary support and resources from the C-suite to strengthen your organization’s digital defenses.
Conclusion
Successful leadership in the realm of cyber security hinges on a combination of visionary foresight, analytical prowess, collaborative efforts across the organization, and effective management of higher-level stakeholders. These qualities are the foundation for guiding an organization through the intricacies of cyber security challenges in today’s ever-evolving digital landscape.




